Security Panels
Security panels provide several functions to coordinate the operation and management of a security system. They can include an integrated keypad or LED indicators. Most designs include a power transformer for converting the AC voltage to a DC voltage for the sensor loop and contain a rechargeable battery for backup if the commercial power fails. A terminal strip provides for the connection of the wiring that connects all the sensors to the controller as well as the external telephone line. Most designs include a printed circuit board containing all the electronics and a microprocessor. It also connects to and controls the siren that is activated when an alarm condition exists.
Security panels are known by numerous names, such as central control box, control panel, alarm panel, and interface panel. They all perform similar functions including controlling and monitoring sensor status, providing power to the system, connecting the telephone line to the monitoring station, and handling the programmable options for the system.
Zone Layout
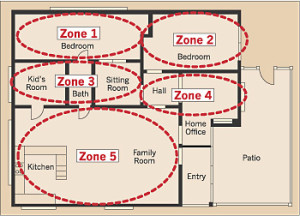
Home security and surveillance systems are usually designed with certain areas of the home designated as zones. A zone can include interior motion detectors or certain rooms or hallways. The use of zones has several purposes. It enables the user to arm only portions of the system, such as the perimeter doors and windows, while bypassing the interior motion detectors when retiring for the night. When leaving the home, all zones, including the interior, can be armed as required.
A zoned security system layout is also used by the external monitoring service to know which sensor in a designated zone is causing the alarm.
If a sensor were to be reported as just sensor 3 zone 5, this could mean just about anywhere at first. But if the sensor were reported as sensor 3 zone 5 perimeter, this would give the operator a better understanding that the violated area is on the outside of the premises. Another reason for using a zoned security system layout is the ease of troubleshooting if a sensor is reported as a bad sensor. For example, if a bad sensor is reported as being in zone 3 perimeter, there is no need to troubleshoot sensors that are located in the interior of the system.
Passwords
Passwords are used as a confirmation tool by most professional alarm monitoring service companies. They are used to avoid a police response when a false alarm situation has been triggered accidentally while still ensuring that the homeowner is safe. The passwords are known only by the residents and the monitoring station personnel. When an alarm condition is received from the home at the monitoring center, the person on duty calls for a police response to the home. However, this occurs only if the alarm is not reset in a predefined length of time. If the alarm is reset at the keypad with the correct code by the owner prior to the time limit, the monitoring station simply calls the subscriber and asks for a password. The password response has two agreed upon formats: One password is used by the homeowner to indicate the alarm condition was accidental and no action need be taken by the monitoring station.
Another secret password is used if the owner is in peril or possibly held hostage by a burglar. This password, when passed after an alarm condition has been reset, results in a police response. This is the option used if the homeowner is asked to respond to the monitoring station phone call by an intruder who (hopefully) does not know the distinction between the two passwords. Passwords are used only if the monitoring station needs to authenticate the cause of an alarm condition when the residents are at home. Law enforcement agencies can penalize homeowners for excessive false alarms.
Common sense should guide the selection of a security system password used with a monitoring service. Never use family or pet names, birth dates, street names, or any word found in the dictionary. The preferred password should include both letters and numbers, and a password should be memorized and never be written down. Numeric keypad codes should also avoid the use of birth dates or home address numbers.
Keypad Locations
Keypads are located by most contractors on the inside wall near the door most often used by the occupants. They are also frequently located in the bedroom to provide easy access by the users when retiring or arising. Keypads used for home security perimeter protection are not recommended for outside mounting because this would allow tampering, vandalism, or attempts by an intruder to search for a correct code. Some exceptions to this rule are applications such as exterior security gates and gated community entrances.
Sensor Locations
Sensors perform all the functions required for detecting and reporting an intrusion in the area they are designed to protect. Window and door sensors are installed on the door or window frame. Window sensors can be protected by either a magnetic switch that detects an opening of the window frame or other types mounted on the window to detect the sound or vibration of broken glass.
Interior surveillance cameras and motion detectors are usually wall mounted and are used to protect open areas where an intruder might be able to defeat the perimeter security system sensors.
Exterior surveillance cameras and security lighting systems should be located in areas near the front, side, and rear entrances to detect intruders before they reach the perimeter security sensors.
Motion Detector Locations
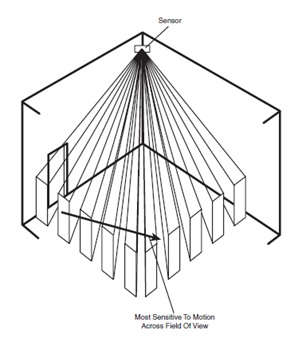
Motion detectors are usually mounted in the corner of a room. This enables the PIR type of motion detector to cover a 90° field. As illustrated in Figure they are sensitive to movement across the sensor field of view.
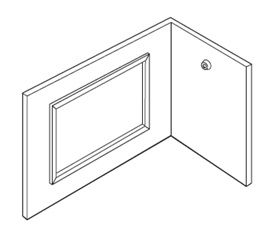
Window Sensor Location
The location of a window sensor can vary with different types of windows. Vibration detectors are mounted on the glass, whereas acoustical window sensors are typically mounted on an adjacent wall, as illustrated in Figure.
- Window Sensor
Alarm Types
Alarm sounders not only attract the attention of others outside the home, but also create a sufficiently high level of sound to discourage an intruder. Various types of sirens, horns, buzzers, klaxons, and bells are used to attract attention when an alarm condition is activated. Different types have varying levels of volume for various locations. Older alarm systems used bells typically mounted on an outside wall. Today bells are rarely used except in commercial buildings for fire alarms. They have been replaced in home security systems by solid-state electronic sirens. These sirens provide a higher level of sound output as well as a variety of tones and sound pitch.
Interior sounders installed in concealed areas in the home operating at maximum sound levels are designed to frighten an intruder into making a fast exit because the sound masks any opportunity to hear an outside approaching police siren. Interior sirens are available from several vendors that operate at sound levels in the 110dB–120dB range, which is near the threshold of pain.
Exterior Security Lighting Systems
Exterior lighting is often used to illuminate dark areas or areas to be protected using motion detection sensors that activate security lighting to deter an intruder. Dark areas surrounding the home where there are trees or shrubs are specific areas that need to be illuminated with security lighting systems. Motion detector-activated lights are also popular for exterior lighting.
Exterior security lighting should be used near landscaped areas around the home, such as shrubs, bushes, foliage, and trees. Security lighting systems used during dark hours avoid the problem of allowing an intruder to enter the area surrounding a home and attempt entry while unobserved in a dark area.
To Know more about Burglar Alarm System, Please Visit http://www.burglaralarm.in/