Biometric Fingerprint Recognition Access Control System
Concept
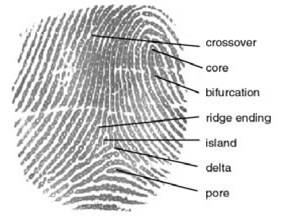
A fingerprint usually appears as a series of dark lines that represent the high,peaking portion of the friction ridge skin,while the valleys between these ridges appears as white space and are the low, shallow portion of the friction ridge skin. Fingerprint identification is based primarily on the minutiae, or the location and direction of the ridge endings and bifurcations (splits) along a ridge path. The images below present examples of fingerprint features: (a) two types of minutiae and (b) examples of other detailed characteristics sometimes used during the automatic classification and minutiae extraction processes.
The types of information that can be collected from a fingerprint’s friction ridge impression include the flow of the friction ridges (Level 1 Detail), the presence or absence of features along the individual friction ridge paths and their sequence (Level 2 Detail), and the intricate detail of a single ridge (Level 3 Detail). Recognition is usually based on the first and second levels of detail or just the latter.
AFIS technology exploits some of these fingerprint features. Friction ridges do not always flow continuously throughout a pattern and often result in specific characteristics such as ending ridges, dividing ridges and dots, or other information. An AFIS is designed to interpret the flow of the overall ridges to assign a fingerprint classification and then extract the minutiae detail – a subset of the total amount of information available yet enough information to effectively search a large repository of fingerprints.
Biometric Hardware
A variety of sensor types — optical, capacitive, ultrasound, and thermal — are used for collecting the digital image of a fingerprint surface. Optical sensors take an image of the fingerprint, and are the most common sensor today. The capacitive sensor determines each pixel value based on the capacitance measured, made possible because an area of air (valley) has significantly less capacitance than an area of finger (friction ridge skin). Other fingerprint sensors capture images by employing high frequency ultrasound or optical devices that use prisms to detect the change in light reflectance related to the fingerprint. Thermal scanners require a swipe of a finger across a surface to measure the difference in temperature over time to create a digital image.
Biometric Software
The two main categories of fingerprint matching techniques are minutiae-based matching and pattern matching. Pattern matching simply compares two images to see how similar they are. Pattern matching is usually used in fingerprint systems to detect duplicates. The most widely used recognition technique, minutiae-based matching, relies on the minutiae points described above, specifically the location and direction of each point.
Why FingerPrint ?
The biometric verification systems that are currently being used include: fingerprint, iris, voice, retina face, hand, vein and signature. Out of all of these, the Iris can return the most accurate results. But since it requires the system or device to come very close to the individual’s eyes, it a less desirable method of verification. In addition, such devices or systems tend to be expensive and bulky, putting limits on its practical application.
A typical voice recognition system is usually more affordable, but it’s not always reliable because the human voice is subject to changes due to illness, hoarseness, or other common throat problems. This system is also subject to extraneous noises in the surrounding area, static, and communication conditions.
Since faces have different dimensions and features depending on the angle, expression and age, a face recognition system is not likely to be of much practical use.
The hand recognition system tends to take too much space and has a high return rate of False Acceptance (FAR). Therefore, this system is rarely used in highly security zones. There are also cost problems in its administration, as well as concerns over access to confidential information.
Vein recognition can guarantee top security because it is almost impossible to duplicate an individual’s vein. But it also has limits in practical application because its hardware structure is extremely complex, and the entire system costs a lot of money.
The results with a signature recognition system, like the voice recognition system, are easily affected by various factors, and therefore it is not reliable at all.
Fingerprint recognition has long been favored among many biometric identification technologies due to its uniqueness and permanence. Nowadays, fingerprint recognition is considered to be the best choice for most applications from network security systems to compact devices, due to its accuracy, speed, reliability, non-intrusive interfaces, and cost-effectiveness, resulting in acquiring 50% of the shares in biometric markets.